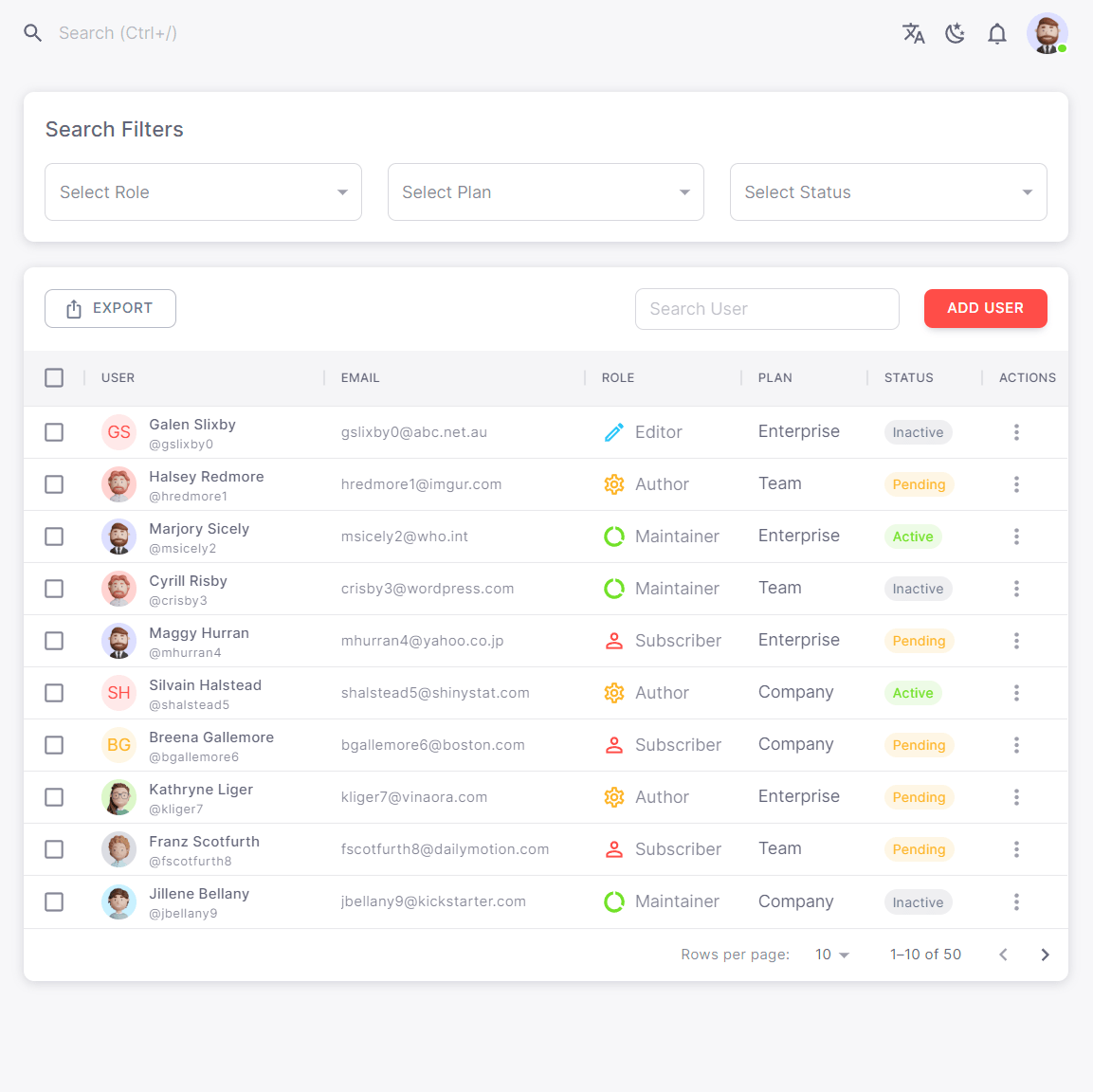
Protect your organization with AllFront Security Model
Everything is going next-gen, why not catch the trend with a fresh look at security?
Govern defenses for each line
Be sure and be ready
Analytics
Lorem ipsum dolor sit amet, consectetur elit, sed do eiusmod tempor dolore magna aliqua enim ad minim veniam.
Automation
Lorem ipsum dolor sit amet, consectetur elit, sed do eiusmod tempor dolore magna aliqua enim ad minim veniam.
Collaboration
Lorem ipsum dolor sit amet, consectetur elit, sed do eiusmod tempor dolore magna aliqua enim ad minim veniam.
See what Saasley can do for your organization.
Get custom solutions for your edge-case problems
We are offering a few out-of-band solutions that could help you in cases where traditional services may not help.
- check_circleWith our "AllFront Security Model", you can get more than just the basic pentest reports.
- check_circleYou can also sign up for our new cyber security training platform and enrich your coworkers with valuable security reflexes.
Proven Performance
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip commodo.
Unparalleled Track Record
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip commodo.
A modern and powerful application
Multiple features, modules, roles, metrics, awards and contests at your disposal.
- check_circlePhysical rewards for successful users to boost interaction
- check_circleContests and leaderboards that allow teams to compete
- check_circleBrowsable solutions for modules such as secure coding
- check_circleAdvanced user/role structure that supports multiple auth schemes
“ We were looking for an innovation partner that could be provide all the components that we needed. SaaS, with its abilities was a good match.”
John Doe
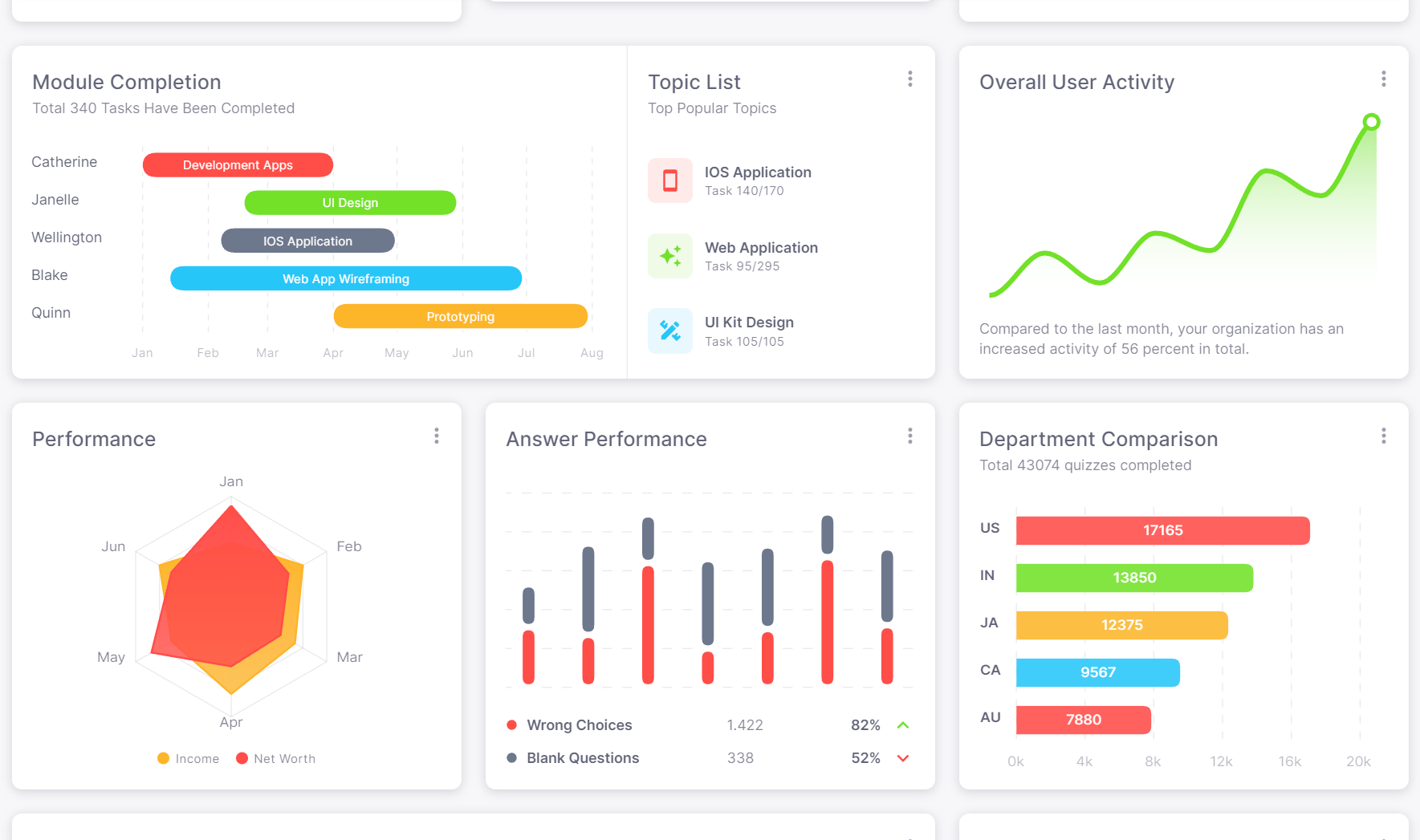
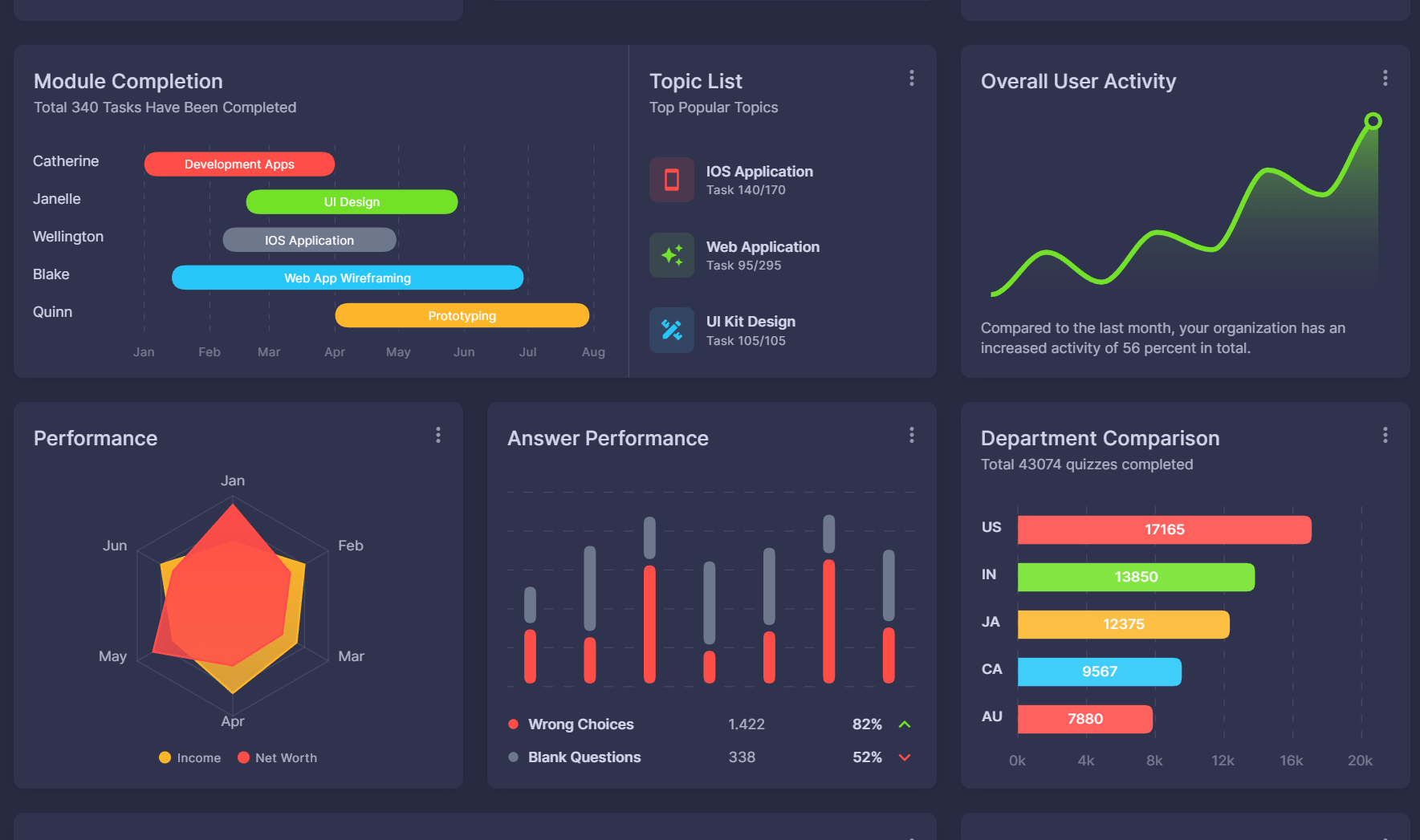
Marketing managerAnalytics that show concrete improvement
Metrics and numbers for both individual and company-wide security performance
- check_circleQuestion answer analysis to show most lacking areas for employees
- check_circleCharts that display improvement of teams and employees
More benefits
Saasley at your fingertips
Analytics
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua.
Collaboration
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua.
Automation
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua.
Secure & Reliable
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua.
Affordable
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua.
24/7 Support
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua.
Pay as you go
Simple pricing plan for you
Secure Coding Module
Starting from best practices and common use cases, this module covers a wide variety of topics regarding secure coding and product development.
- check_circleMultiple programming languages
- check_circleVulnerabilities explained in detail
- check_circleRemediation types and effects
- check_circleCI/CD Security & Shift-Left
- check_circleSecure Development Lifecycle
- check_circleCase studies and solutions
- check_circleContent for backend and frontend
- check_circleConsultancy from our security team
Infrastructure Module
Infrastructure security best practices, pitfalls, infrastucture automation and cloud architecture security are all included within this module.
- check_circleCommon threats for infrastructure
- check_circleProtection mechanisms for threats
- check_circleEffective infrastructure defenses
- check_circleIncident response basics & forensics
- check_circleForensics with non-repudiation
- check_circleCloud security modules
- check_circleConsultancy from our security team
Security Leadership Module
For effective management of security teams, this module is recommended for leaders and managers. Topics such as importance of keeping team members balanced between boredom and stress are covered in this module.
- check_circleTeam building & structuring
- check_circleEffective management for security
- check_circleBug bounty programs
- check_circleInter-team communication
- check_circleCreating a security product portfolio
- check_circleManaging security breaches
- check_circleCertification & compliance
- check_circleTeam utilization against quiet quitting
Administration Module
Organizational administration and control is one of the most crucial fields for a company to operate properly. Safeguarding company assets with necessary access controls is a prime topic for this module.
- check_circleDevice inventory control
- check_circleRemote working and personal use
- check_circleProvisioning for computers and phones
- check_circleMobile device management
- check_circleIdentity providers, SSO and 2FA
- check_circleProper onboarding and offboarding
Hiring Module
Building a team of engineers is no easy task, especially if being done from ground up. Choosing / eliminating candidates alongside keeping the team functional and happy can only be achieved via good people operation principles.
- check_circleSchema of a good hiring process
- check_circleDo's and don'ts for peope operations
- check_circleNecessary requirements for security roles
- check_circleOrganization size and corresponding team roles
- check_circleDealing with toxicity
- check_circleThe concept of team-fit
Security-Friendly Design Module
One of the least-thought areas of development, designing and planning a UX with security in mind is also a part of this training program. Convincing users to take security into consideration without scaring them away boosts security standing greatly.
- check_circleSecurity friendly design principles
- check_circleIndications of danger and safety
- check_circleComponents, colors and sounds
- check_circleEncouraging user feedback
- check_circleCorrect wording for user actions